Definition of Spear Phishing:
Spear-phishing is a targeted attempt to steal sensitive information such as account credentials or financial information from a specific victim, often
for malicious reasons. This is achieved by acquiring personal details on the victim such as their friends, hometown, employer, locations they
frequent, and what they have recently bought online. The attackers then disguise themselves as a trustworthy friend or entity to acquire sensitive
information, typically through email or other online messaging. This is the most successful form of acquiring confidential information on the
internet, accounting for 91% of attacks.
Example:
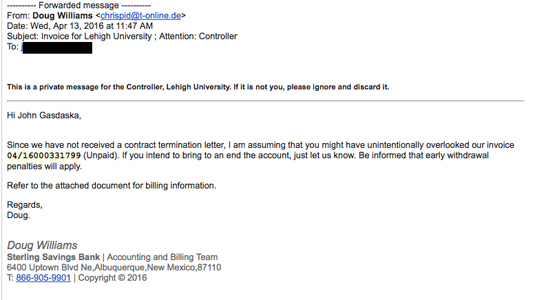
The email look s authentic, but it's not.
Spear-phishing vs. Phishing
Spear-phishing can easily be confused with phishing because they are both online attacks on users that aim to acquire confidential information.
Phishing is a broader term for any attempt to trick victims into sharing sensitive information such as passwords, usernames, and credit card
details for malicious reasons. The attackers often disguise themselves as a trustworthy entity and make contact with their target via email, social
media, phone calls (often called “vishing” for voice-phishing), and even text messages (often called “smishing” for SMS-phishing).
Unlike spear-phishing attacks, phishing attacks are not personalized to their victims, and are usually sent to masses of people at the same time.
The goal of phishing attacks is to send a spoofed email (or other communication) that looks as if it is from an authentic organization to a large
number of people, banking on the chances that someone will click on that link and provide their personal information or download malware.
Spear-phishing attacks target a specific victim, and messages are modified to specifically address that victim, purportedly coming from an entity
that they are familiar with and containing personal information. Spear-phishing requires more thought and time to achieve than phishing. Spearphishing
attackers try to obtain as much personal information about their victims as possible to make the emails that they send look legitimate
and to increase their chance of fooling recipients. Because of the personal level of these emails, it is more difficult to identify spear-phishing
attacks than to identify phishing attacks conducted at a wide scale. This is why spear-phishing attacks are becoming more prevalent.
How does spear-phishing work?
The act of spear-phishing may sound simple, but spear-phishing emails have improved within the past few years and are now extremely difficult
to detect without prior knowledge on spear-phishing protection. Spear-phishing attackers target victims who put personal information on the
internet. They might view individual profiles while scanning a social networking site. From a profile, they will be able to find a person’s email
address, friends list, geographic location, and any posts about new gadgets that were recently purchased. With all of this information, the attacker
would be able to act as a friend or a familiar entity and send a convincing but fraudulent message to their target.
To increase success rates, these messages often contain urgent explanations on why they need sensitive information. Victims are asked to open
a malicious attachment or click on a link that takes them to a spoofed website where they are asked to provide passwords, account numbers,
PINs, and access codes. An attacker posing as a friend might ask for usernames and passwords for various websites, such as Facebook, so that
they would be able to access posted photos. In reality, the attackers will use that password, or variations of it, to access different websites that
have confidential information such as credit card details or Social Security Numbers. Once criminals have gathered enough sensitive information,
they can access bank accounts or even create a new identity using their victim’s information. Spear-phishing can also trick people into
downloading malware or malicious codes after people click on links or open attachments provided in messages.
6 tips to avoid a spear-phishing attack:
- Watch what personal information you post on the internet: Look at your online profiles. How much personal information is available for potential attackers to view? If there is anything that you do not want a potential scammer to see, do not post it – or at the very minimum make sure that you’ve configured privacy settings to limit what others can see.
- Have smart passwords: Do not just use one password or variations of passwords for every account that you own. Reusing passwords or password variations means that if an attacker has access to one of your passwords, they effectively have access to all of your accounts. Every password that you have should be different from the rest – passwords with random phrases, numbers, and letters are the most secure.
- Frequently update your software: If your software provider notifies you that there is a new update, do it right away. The majority of software systems include security software updates that should help to protect you from common attacks. Where possible, enable automatic software updates.
- Do not click links in emails: If an organization, such as your bank, sends you a link, launch your browser and go directly to the bank’s site instead of clicking on the link itself. You can also check the destination of a link by hovering your mouse over it. If the URL does not match the link’s anchor text or the email’s stated destination, there is a good chance that it could be malicious. Many spear-phishing attackers will try to obfuscate link destinations by using anchor text that looks like a legitimate URL.
- Use logic when opening emails: If you get an email from a “friend” asking for personal information including your password, carefully check to see if their email address is one that you have seen them use in the past. Real businesses will not send you an email asking for your username or password. Your best bet would be to contact that “friend” or business outside of email, or visit the business’ official website to see if they were the party who actually contacted you.
- Implement a data protection program at your organization or for your home use: A data protection program that combines user education around data security best practices and implementation of a data protection solution will help to prevent data loss due to spear-phishing attacks. For midsize to larger corporations, data loss prevention software should be installed to protect sensitive data from unauthorized access or egress, even if a user falls for a phishing scam.
Geezz! I wish I wrote this article! But alas, I borrowed it from here:
The bottom line is about Education. The more you are informed, the safer you will be.
Be careful what you post on Social Media Sites. I personally am not on any Social Media Sites. If I want to contact someone, I call them.


